
Customer Access & Identity Management
Harness the power of seamless identity management with our revolutionary CIAM platform.
How does it work?
Streamline Access & Identity management with Metrics Matter
Configure Organizations
Establish the organizational structure and invite colleagues to collaborate.
Setup Users & Groups
Securely onboard and offboard B2B users to access data through your platform.
Set Policy
Charge your customers as you like be it Subscription, One-Time or Adhoc, we’ve got you covered.
Manage
Self-serve product with engine of growth analytics to help you securely and easily onboard users, offer subscriptions and manage billing.
Centralize all operations in one place
Empower your business with a self-service solution equipped with growth analytics to effortlessly onboard users, provide subscription options, and securely streamline billing management.
Onboarding
We facilitate the onboarding of new B2B customers and organizations on your behalf through a user-friendly self-serve process that enhances conversion rates.
- Streamlined Onboarding
- Improved Conversion Rates
- Enhanced Efficiency
- Business Growth
- Customer Commitment
Identity Management
Effectively oversee the entire user identity lifecycle within your organization.
- Complete Identity Lifecycle Management
- End-to-End Control
- Enhanced Security and Compliance
- Streamlined Access
Access Management
Ensure a secure and seamless login experience by employing the suitable authorization method for your applications.
- Secure and User-Friendly Login
- Tailored Authorization Methods
- Enhanced Security and Convenience
- User Satisfaction and Engagement
- Combine different authorization methods
Authentication
Deliver a seamless and secure login process by enabling authentication through a variety of standard providers.
- Flexible User Login Experience
- Multiple Well-Known Providers
- Smooth and Secure Process
- User-Friendly Environment
- Positive and Secure User Experience
Driven by results, not features
Despite an impressive feature list, we do not aspire to be a leader in any of the areas.
We ensure our processing meets all your legal, security, privacy, and financial requirements and provide you with the metrics you need to maximize conversion.
Although we offer a wide range of features, we don't aim to dominate any particular area. Our primary goal is to help you achieve your desired outcomes, specifically by boosting the adoption of your online services.
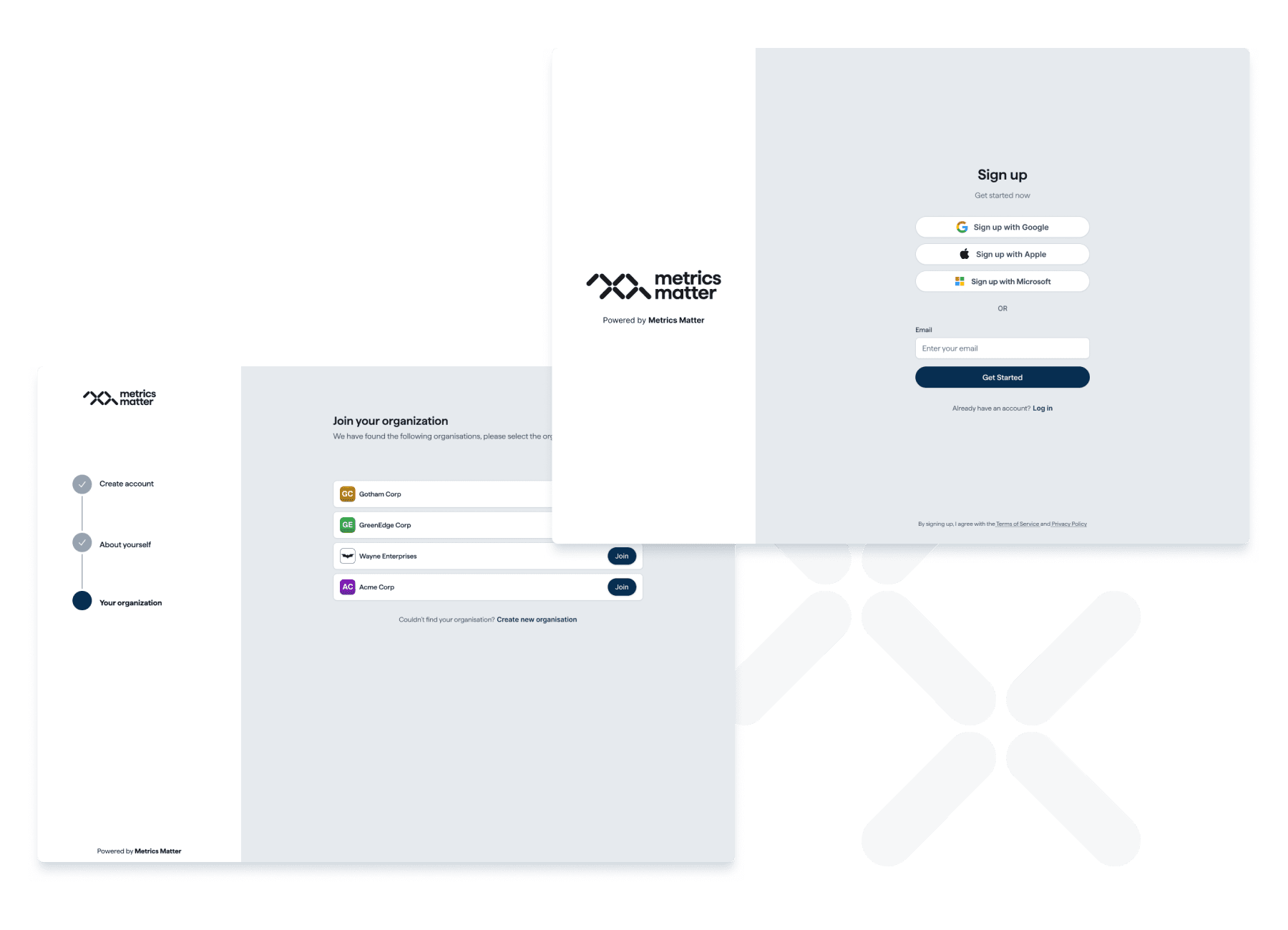
Onboarding
Our platform simplifies and streamlines the onboarding of new customers and organizations on your behalf, reducing friction and improving conversion rates. This is achieved through an intuitive self-serve process that guides users seamlessly from their initial interactions with your services to successful onboarding. By providing a user-friendly experience, we enhance the likelihood of customers committing to your offerings. Our solution not only saves time but also boosts the efficiency and effectiveness of the onboarding process, ultimately contributing to your business's growth and success.
Easily create accounts using Google, Microsoft, Apple, and other sign-up methods.
- Diverse Sign-up Methods: Our platform supports various sign-up options like Google, Microsoft, Apple, and more.
- Convenient User Experience: Choose your preferred sign-up for a familiar, easy experience.
- Quick and Hassle-free Account Creation: Our quick, easy setup enhances user satisfaction and engagement.
- Attracting a Broad User Base: Versatile sign-up options bolster user diversity and platform success.
- User-Centric Approach: Our seamless sign-up process is tailored for user satisfaction.
Collect user and organization information only when necessary, gradually building comprehensive profiles over time without overwhelming customers with upfront questions.
- Gradual Information Collection: Our approach involves gradually collecting user and organization information.
- Minimized Upfront Overload: We gather only what's necessary at each step, avoiding upfront overload.
- Seamless User Experience: This strategy creates a seamless user experience, allowing comprehensive profiles to develop gradually.
- User-Friendly Data Gathering: Customers are not overwhelmed, and information is collected in a user-friendly manner over time.
Enhance user and organization data accuracy and streamline customer interactions by pre-filling and validating information through third-party data providers.
- Efficient Data Collection: Our solution improves data collection efficiency and accuracy.
- Third-Party Data Integration: We leverage third-party data suppliers to pre-fill and validate user and organization information.
- Accurate and Up-to-Date Data: This integration ensures data accuracy and reduces the number of customer steps.
- User-Friendly Experience: Customers benefit from a smoother, more user-friendly experience while data integrity is maintained.
- With a single integration with Metrics Matter: You can access a network of data providers and validators.
Identity Management
Empower your organization to efficiently and comprehensively manage every aspect of the user identity lifecycle. This means from the moment a user joins your organization to their ongoing access and role changes, and finally to the secure and appropriate deactivation of their account when they depart.
Our solution provides you with the tools and processes to ensure that user identities are maintained and governed in a manner that aligns with your organization's security, compliance, and operational requirements. By managing the complete identity lifecycle, you can enhance security, streamline access, and maintain control throughout each stage of the user's journey within your organization.
Streamline your user experience with single sign-in, offering easy and secure access across multiple platforms and services.
- Single Sign-In Efficiency: Our solution simplifies access to multiple services with a single sign-in.
- Centralized Authentication: Our centralized authentication streamlines navigation and access across your digital ecosystem.
- Enhanced Security: Our platform ensures stronger security with a unified system for user authentication and access.
- Simplified User Journey: Streamlined login enhances navigation and satisfaction across apps and services.
Adopt a dynamic organizational structure to streamline user management, using organizational units and user groups for efficient role assignments and access control.
- Dynamic Organizational Structure: Our platform boosts user management with a dynamic structure.
- Organizational Units and User Groups: Leverage organizational units and user groups for real-world alignment.
- Streamlined Role Assignments: This method simplifies role assignments and access control for more efficient user management.
- Reflective of Organizational Structure: Our solution aligns user management with your organizational structure, enhancing efficiency.
Enhance user management efficiency by aligning your organizational structure with real-world needs, utilizing organizational units, user groups, and sub-organizations.
- Unified Access Oversight: Our platform offers an efficient means to oversee user access through a unified dashboard.
- Comprehensive Permission Management: Maintain a comprehensive permission overview, aligning with roles and responsibilities.
- Enhanced Security:Our unified access management boosts security, minimizes errors, and protects privacy.
- Seamless User Experience: Seamless user experiences ensure easy compliance and data privacy for organizations.
Support for user grouping to align with your organization's operational structure, enabling users to be categorized based on their work processes.
- Customized User Grouping: Our platform facilitates user grouping that aligns with your organization's operational dynamics.
- Tailored User Organization: Users can be organized to mirror the specific workflows and structures within your company.
- Streamlined Access Control: This feature streamlines access control, role assignments, and permissions, enhancing efficiency.
- Harmonized User Management: Customization boosts user management, productivity, and security.
Empower users with control over their data, offering them continuous access to their data and transaction history.
- User Data Autonomy: We empower users to take control of their data, allowing them to manage and access it independently.
- Transparency and Trust: This approach fosters transparency, trust, and accountability by giving users autonomy over their data.
- Informed Decision-Making: Users make informed decisions, safeguarding their personal data.
- Enhanced User Experience: This control boosts the user experience by prioritizing empowerment and privacy.
Accounts can be shared among individuals belonging to multiple organizations and applications, simplifying context switching and eliminating the need to remember multiple sets of credentials.
- Re-usable User Accounts: Our system enables the reuse of user accounts across multiple organizations.
- Seamless Context Switching: Switch easily between organizations without juggling multiple logins.
- Time and Convenience Savings: This streamlined approach saves time and enhances user convenience.
- Effortless Navigation: Effortless and secure, our login streamlines navigation for a hassle-free experience.
Simplify the process of inviting new users to your organization by automatically placing them in the appropriate location based on their email address.
- Automated User Onboarding: We streamline user onboarding by automating user placement based on email addresses.
- Seamless Integration: Our system seamlessly assigns new users to the correct departments or teams.
- Enhanced Productivity: This automation ensures new users have immediate access to essential resources, boosting productivity.
- Efficiency and Accuracy: Cut down on manual work, lower mistakes, and streamline the onboarding process for everyone involved.
Introduce supplementary security measures by including extra steps in the authentication process.
- Enhanced Security Layers: Our system enhances security by introducing additional layers into the authentication process.
- Multifactor Authentication: We provide multifactor authentication methods like TOTP to fortify verification.
- Protection from Unauthorized Access: These measures safeguard accounts and data, minimizing unauthorized access risks.
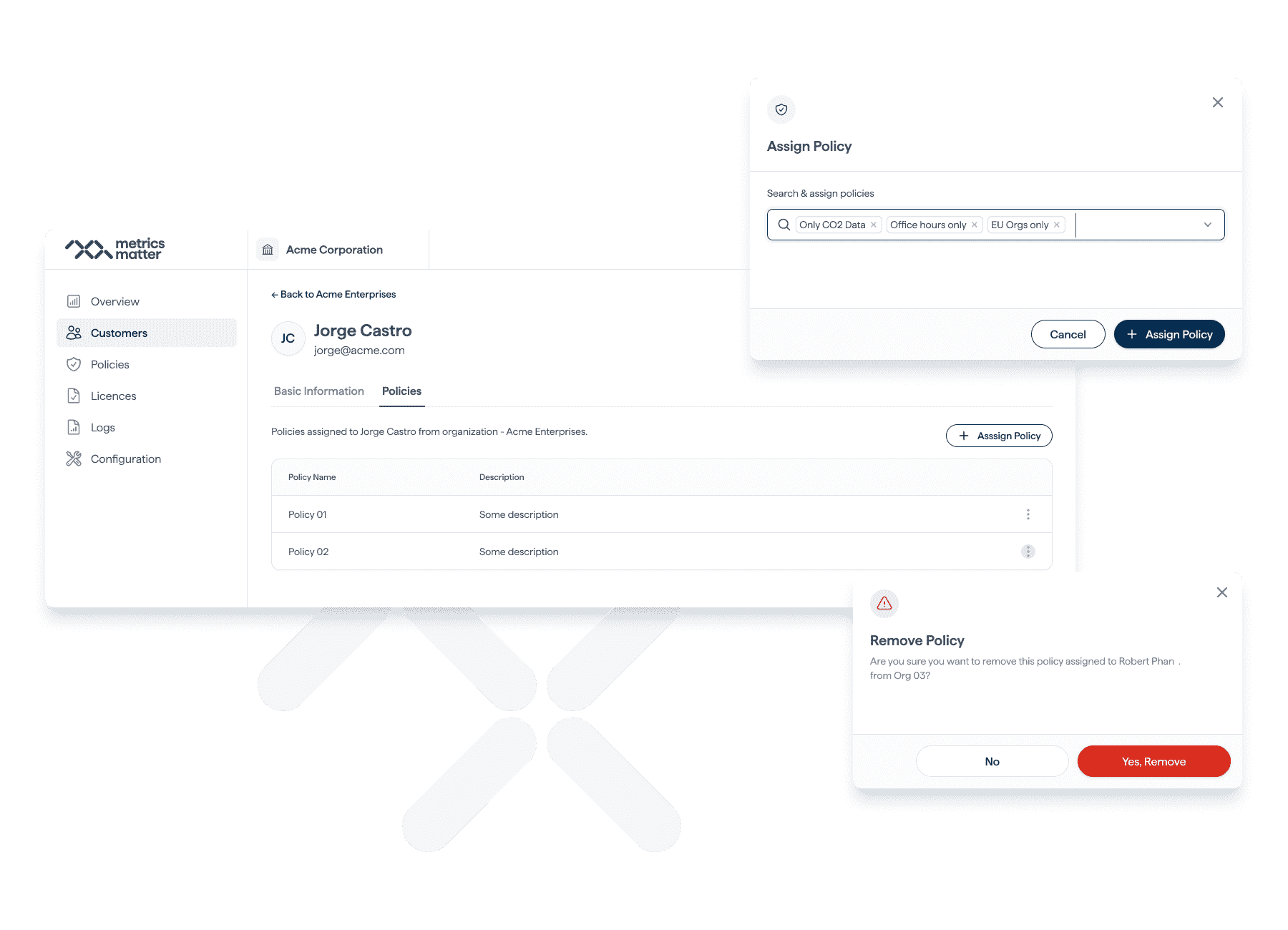
Access Management
Deliver a login experience that is both secure and user-friendly by selecting the right authorization method for your specific applications. Whether it's through username and password, single sign-on (SSO), biometrics, or other authentication methods, tailoring the authorization process enhances the security and convenience of user access. By making this choice, you not only protect sensitive data but also optimize the user experience, increasing user satisfaction and engagement. It's all about striking the perfect balance between security and ease of use.
Grant access in accordance with policies that define the criteria for user access approval.
- Policy-Driven Access Control: Our system controls access via policies that specify user access conditions.
- Guidelines for Authorization: These policies set access criteria based on roles, permissions, and timing.
- Structured and Secure Approach: With policies, you ensure a secure access system, reducing unauthorized access.
- Enhanced Security: This method boosts security and streamlines the authorization process.
Access is determined by evaluating the specific attributes of the user or organization seeking to log in. These attributes can include factors such as user roles, affiliations, credentials, and organizational characteristics. By assessing these attributes, the system can make informed decisions about access privileges, ensuring that the right individuals or entities gain entry to the appropriate resources. This approach enhances security, as access is contingent on the verifiable attributes of the user or organization, reducing the risk of unauthorized access and maintaining the integrity of your system.
- Attribute-Based Access Evaluation: Our system evaluates user or organization attributes to determine access.
- Informed Access Decisions: Attributes like user roles, affiliations, credentials, and organizational characteristics inform access decisions.
- Security Enhancement: This approach enhances security by granting access based on verifiable attributes, reducing unauthorized access risk.
- System Integrity Maintenance: By ensuring that the right individuals or entities gain access to appropriate resources, we maintain the integrity of your system.
Access is determined by the specific role or roles assigned to a user within the system. Each role carries defined permissions and responsibilities, and access is governed by these role-based rules. This approach simplifies access control, as users are only given the permissions necessary for their roles, reducing the risk of unauthorized access to sensitive resources. By aligning access with roles, organizations can efficiently manage user privileges, enhance security, and maintain compliance, ensuring that users can perform their tasks effectively and securely within the system.
- Role-Based Access Control: Access is determined by the specific role or roles assigned to a user within the system.
- Defined Permissions and Responsibilities: Each role carries defined permissions and responsibilities, governing access.
- Simplified Access Control: This approach simplifies access control by granting permissions based on roles, reducing unauthorized access risk.
- Efficient Privilege Management: Organizations efficiently manage user privileges, enhance security, and maintain compliance.
- Effective and Secure User Task Performance: Users can perform tasks effectively and securely within the system, aligned with their roles.
Explicitly control the access of your applications to external services to eliminate any ambiguity when assigning the appropriate permissions, ensuring a clear distinction between applications and actual users.
- Proactive Application Access Control: We adopt a proactive approach to managing application access to external services.
- Clear and Explicit Control: Our system establishes clear and explicit control mechanisms, minimizing confusion in permissions.
- Separation of Applications and Users: This approach maintains a clear distinction between applications and real users, bolstering security and streamlining authorization.
- Permissions Tailored to Functionality: Each application is granted only the necessary permissions, reducing overreach and unauthorized access.
- Digital Environment Safeguarding: We ensure the safety of your organization's digital environment through these control mechanisms.
Easily receive and assess access requests from your users for applications your organization already has access to, and from your customers when you are not offering any plans. Approving or denying access based on these requests is a straightforward and speedy process.
- Effortless Access Request Management: Our system allows you to effortlessly manage access requests.
- User and Customer Access: This includes requests from both your users and customers.
- Prompt Review Process: Access requests are promptly reviewed for ease and efficiency.
- Responsive and User-Friendly Experience: This approach fosters a responsive and user-friendly experience for users and customers.
- Agile Adaptation: It simplifies access control and promotes agility in meeting users' evolving requirements.
Utilize context parameters as a robust security measure when evaluating authorization requests. By taking into account the specific context of each user, this approach acts as a critical safeguard against unauthorized access. It ensures that access permissions are dynamically adapted to the unique circumstances of each user, reducing the risk of data breaches or unauthorized actions. This contextualized authorization strategy enhances security by precisely tailoring access control and maintaining a more comprehensive and adaptive security framework.
- Context Parameters for Robust Security: We offer the use of context parameters as a robust security measure.
- User-Specific Context Evaluation: This approach evaluates authorization requests by considering each user's specific context.
- Safeguard Against Unauthorized Access: It acts as a critical safeguard against unauthorized access, dynamically adapting access permissions.
- Reduced Risk of Data Breaches: Contextualized authorization reduces the risk of data breaches or unauthorized actions.
- Comprehensive and Adaptive Security: This strategy enhances security by tailoring access control to individual circumstances, maintaining a more adaptive security framework.
Frequently asked questions
Is there a free trial available?
At no cost to you, our fundamental services are available for use. This includes Onboarding, Customer Identity & Access Management system, and our Contracting and Compliance services – all at zero expense.
Is your solution limited in any way?
Rest assured, Metrics Matter's Customer Identity & Access Management solution has no restrictions. Feel free to add as many users, organizations, or units as you need without any surprises or limitations.
How can such an extensive solution be free of charge?
In our dedication to building a sustainable society, we provide all non-financial capabilities at no cost while maintaining a fully for-profit business model through our premium services.
When will Subscription Management be released?
This summer marks a significant milestone for our team and clients, as we gear up for the much-anticipated launch of our cutting-edge functionalities: Subscription Management, Contracting, and Compliance. This trio of enhancements is designed to revolutionize the way businesses manage their operations, offering unparalleled efficiency, security, and ease of use.
Is the beta release available for everyone?
The Beta version of CIAM is designed for real-world testing and is open to anyone willing to provide us with insightful feedback.
Coming soon
Metrics Matter's Customer Identity & Access Management (CIAM) solution is set to debut with a beta version very soon.
The full release of Metrics Matter's platform, scheduled for the summer, will include additional modules for Subscription Management, Contracting, and Compliance. These modules will provide businesses with the tools they need to manage subscriptions, contracts, and compliance requirements in a centralized and efficient manner.